EC-Council 412-79v10 Study Guides 2021
We provide which are the best for clearing 412-79v10 test, and to get certified by EC-Council EC-Council Certified Security Analyst (ECSA) V10. The covers all the knowledge points of the real 412-79v10 exam. Crack your EC-Council 412-79v10 Exam with latest dumps, guaranteed!
Online 412-79v10 free questions and answers of New Version:
NEW QUESTION 1
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
- A. SDW Encryption
- B. EFS Encryption
- C. DFS Encryption
- D. IPS Encryption
Answer: B
NEW QUESTION 2
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.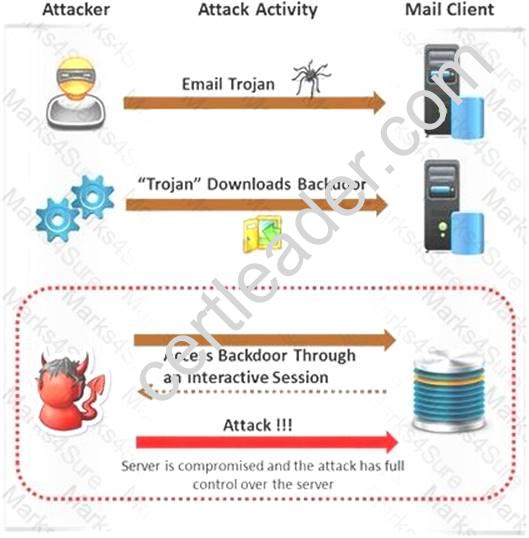
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
- A. Internal network mapping to map the internal network of the target machine
- B. Port scanning to determine what ports are open or in use on the target machine
- C. Sniffing to monitor all the incoming and outgoing network traffic
- D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Answer: D
NEW QUESTION 3
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 4
What is the difference between penetration testing and vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
- B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer: A
NEW QUESTION 5
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 6
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
NEW QUESTION 7
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
- A. 802.11b
- B. 802.11a
- C. 802.11n
- D. 802.11-Legacy
Answer: D
NEW QUESTION 8
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 9
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
- A. TCP port 152
- B. UDP port 177
- C. UDP port 123
- D. TCP port 113
Answer: C
NEW QUESTION 10
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
- A. Searching for web page posting patterns
- B. Analyzing the link popularity of the company’s website
- C. Searching for trade association directories
- D. Searching for a company’s job postings
Answer: D
NEW QUESTION 11
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum.
Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
Which of the following ICMP messages will be generated if the destination port is not reachable?
- A. ICMP Type 11 code 1
- B. ICMP Type 5 code 3
- C. ICMP Type 3 code 2
- D. ICMP Type 3 code 3
Answer: D
NEW QUESTION 12
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.
What are the two types of ‘white-box’ penetration testing?
- A. Announced testing and blind testing
- B. Blind testing and double blind testing
- C. Blind testing and unannounced testing
- D. Announced testing and unannounced testing
Answer: D
NEW QUESTION 13
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
- A. Smurf scan
- B. Tracert
- C. Ping trace
- D. ICMP ping sweep
Answer: D
NEW QUESTION 14
War Driving is the act of moving around a specific area, mapping the population of wireless access points for statistical purposes. These statistics are then used to raise awareness of the security problems associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector) problem
documented with static WEP?
- A. Airsnort
- B. Aircrack
- C. WEPCrack
- D. Airpwn
Answer: A
NEW QUESTION 15
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer: B
NEW QUESTION 16
To locate the firewall, SYN packet is crafted using Hping or any other packet crafter and sent to the firewall. If ICMP unreachable type 13 message (which is an admin prohibited packet) with a source IP address of the access control device is received, then it means which of the following type of firewall is in place?
- A. Circuit level gateway
- B. Stateful multilayer inspection firewall
- C. Packet filter
- D. Application level gateway
Answer: C
NEW QUESTION 17
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 18
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
- A. Special-Access Policy
- B. User Identification and Password Policy
- C. Personal Computer Acceptable Use Policy
- D. User-Account Policy
Answer: B
NEW QUESTION 19
What are the 6 core concepts in IT security?
- A. Server management, website domains, firewalls, IDS, IPS, and auditing
- B. Authentication, authorization, confidentiality, integrity, availability, and non-repudiation
- C. Passwords, logins, access controls, restricted domains, configurations, and tunnels
- D. Biometrics, cloud security, social engineering, DoS attack, viruses, and Trojans
Answer: B
P.S. 2passeasy now are offering 100% pass ensure 412-79v10 dumps! All 412-79v10 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/412-79v10/ (201 New Questions)