Validated 412-79v10 Dumps 2021
We provide in two formats. Download PDF & Practice Tests. Pass EC-Council 412-79v10 Exam quickly & easily. The 412-79v10 PDF type is available for reading and printing. You can print more and practice many times. With the help of our product and material, you can easily pass the 412-79v10 exam.
Free 412-79v10 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.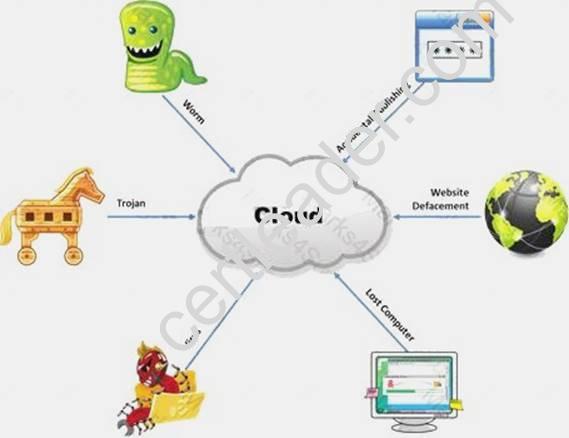
What is the biggest source of data leaks in organizations today?
- A. Weak passwords and lack of identity management
- B. Insufficient IT security budget
- C. Rogue employees and insider attacks
- D. Vulnerabilities, risks, and threats facing Web sites
Answer: C
NEW QUESTION 2
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise themselves as usual network traffic?
- A. Connect Scanning Techniques
- B. SYN Scanning Techniques
- C. Stealth Scanning Techniques
- D. Port Scanning Techniques
Answer: C
NEW QUESTION 3
In a virtual test environment, Michael is testing the strength and security of BGP using multiple routers to mimic the backbone of the Internet. This project will help him write his doctoral thesis on "bringing down the Internet".
Without sniffing the traffic between the routers, Michael sends millions of RESET packets to the routers in an attempt to shut one or all of them down. After a few hours, one of the routers finally shuts itself down. What will the other routers communicate between themselves?
- A. More RESET packets to the affected router to get it to power back up
- B. RESTART packets to the affected router to get it to power back up
- C. The change in the routing fabric to bypass the affected router
- D. STOP packets to all other routers warning of where the attack originated
Answer: C
NEW QUESTION 4
Which of the following attacks does a hacker perform in order to obtain UDDI information such as businessEntity, businesService, bindingTemplate, and tModel?
- A. Web Services Footprinting Attack
- B. Service Level Configuration Attacks
- C. URL Tampering Attacks
- D. Inside Attacks
Answer: A
NEW QUESTION 5
Which of the following methods is used to perform server discovery?
- A. Banner Grabbing
- B. Who is Lookup
- C. SQL Injection
- D. Session Hijacking
Answer: B
NEW QUESTION 6
What is the target host IP in the following command?
- A. Firewalk does not scan target hosts
- B. 172.16.28.95
- C. This command is using FIN packets, which cannot scan target hosts
- D. 10.10.150.1
Answer: A
NEW QUESTION 7
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer: C
NEW QUESTION 8
Which of the following scan option is able to identify the SSL services?
- A. –sS
- B. –sV
- C. –sU
- D. –sT
Answer: B
NEW QUESTION 9
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
- A. 6566 TCP port
- B. 6771 TCP port
- C. 6667 TCP port
- D. 6257 TCP port
Answer: C
NEW QUESTION 10
The objective of this act was to protect consumers personal financial information held by financial institutions and their service providers.
- A. HIPAA
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act
- D. California SB 1386a
Answer: C
NEW QUESTION 11
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
- A. DNSSEC
- B. Firewall
- C. Packet filtering
- D. IPSec
Answer: A
NEW QUESTION 12
Logs are the record of the system and network activities. Syslog protocol is used for delivering log information across an IP network. Syslog messages can be sent via which one of the following?
- A. UDP and TCP
- B. TCP and SMTP
- C. SMTP
- D. UDP and SMTP
Answer: A
NEW QUESTION 13
Which of the following statement holds true for TCP Operation?
- A. Port numbers are used to know which application the receiving host should pass the data to
- B. Sequence numbers are used to track the number of packets lost in transmission
- C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
- D. Data transfer begins even before the connection is established
Answer: D
NEW QUESTION 14
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
- A. intitle:"exchange server"
- B. outlook:"search"
- C. locate:"logon page"
- D. allinurl:"exchange/logon.asp"
Answer: D
NEW QUESTION 15
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
- A. 2.4 Ghz Cordless phones
- B. Satellite television
- C. CB radio
- D. Computers on his wired network
Answer: A
NEW QUESTION 16
John, a penetration tester from a pen test firm, was asked to collect information about the host file in a Windows system directory. Which of the following is the location of the host file in Window system directory?
- A. C:WindowsSystem32Boot
- B. C:WINNTsystem32driversetc
- C. C:WINDOWSsystem32cmd.exe
- D. C:WindowsSystem32restore
Answer: B
NEW QUESTION 17
A penetration test consists of three phases: pre-attack phase, attack phase, and post-attack phase.
Active reconnaissance which includes activities such as network mapping, web profiling, and perimeter mapping is a part which phase(s)?
- A. Post-attack phase
- B. Pre-attack phase and attack phase
- C. Attack phase
- D. Pre-attack phase
Answer: D
NEW QUESTION 18
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
- A. Analyzing, categorizing and prioritizing resources
- B. Evaluating the existing perimeter and internal security
- C. Checking for a written security policy
- D. Analyzing the use of existing management and control architecture
Answer: C
NEW QUESTION 19
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
- A. Vulnerabilities checklists
- B. Configuration checklists
- C. Action Plan
- D. Testing Plan
Answer: A
100% Valid and Newest Version 412-79v10 Questions & Answers shared by Simply pass, Get Full Dumps HERE: https://www.simply-pass.com/EC-Council-exam/412-79v10-dumps.html (New 201 Q&As)