A Review Of 100% Correct MS-102 Exam Question
we provide Downloadable Microsoft MS-102 exam guide which are the best for clearing MS-102 test, and to get certified by Microsoft Microsoft 365 Administrator Exam. The MS-102 Questions & Answers covers all the knowledge points of the real MS-102 exam. Crack your Microsoft MS-102 Exam with latest dumps, guaranteed!
Microsoft MS-102 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
You have a Microsoft 365 E5 tenant that uses Microsoft Intune.
You need to ensure that users can select a department when they enroll their device in Intune.
What should you create?
- A. scope tags
- B. device configuration profiles
- C. device categories
- D. device compliance policies
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/mem/intune/enrollment/device-group-mapping
NEW QUESTION 2
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to create a policy that will generate an email alert when a banned app is detected requesting permission to access user information or data in the subscription.
What should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.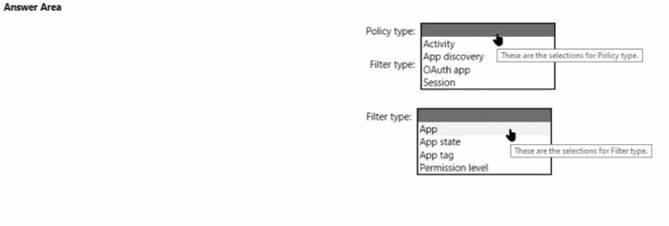
Solution:
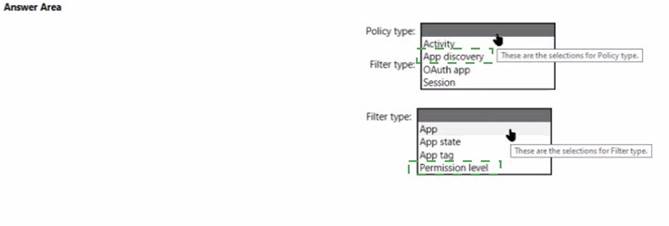
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
DRAG DROP
Your company has an Azure AD tenant named contoso.onmicrosoft.com.
You purchase a domain named contoso.com from a registrar and add all the required DNS records.
You create a user account named User1. User1 is configured to sign in as userl@contoso.onmicrosoft.com.
You need to configure User1 to sign in as user1@contoso.com.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
Your company has a Microsoft 365 subscription. you implement sensitivity Doris for your company.
You need to automatically protect email messages that contain the word Confidential m the subject line.
What should you create?
- A. a sharing policy from the Exchange admin center
- B. a mail flow rule from the Exchange admin center
- C. a message Dace from the Microsoft 365 security center
- D. a data loss prevention (DLP) policy from the Microsoft 365 compliance center
Answer: B
NEW QUESTION 5
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
The subscription contains the users shown in the following table.
In Azure AD, you configure the External collaboration settings as shown in the following exhibit.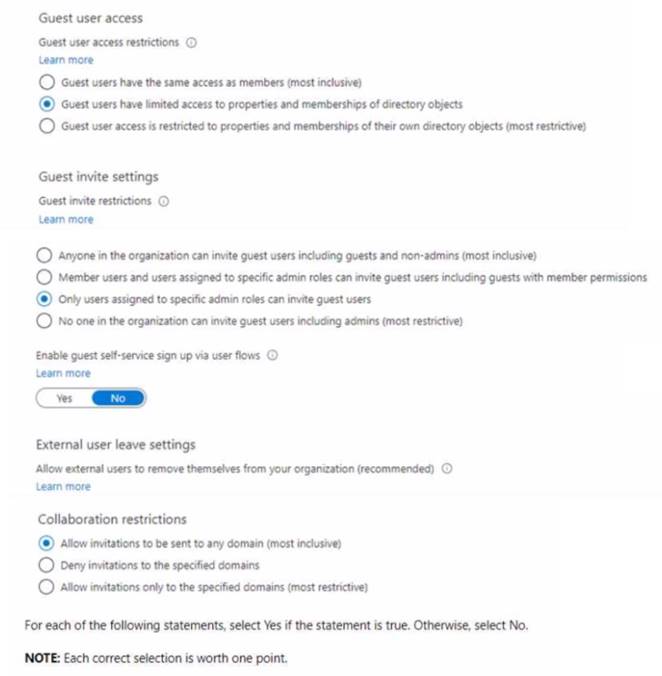
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
HOTSPOT
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.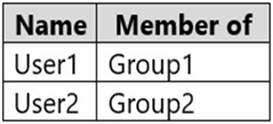
You purchase the devices shown in the following table.
In Microsoft Endpoint Manager, you create an enrollment status page profile that has the following settings:
✑ Show app and profile configuration progress: Yes
✑ Allow users to collect logs about installation errors: Yes
✑ Only show page to devices provisioned by out-of-box experience (OOBE): No
✑ Assignments: Group2
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 7
HOTSPOT
You have a Microsoft 365 E5 tenant that uses Microsoft Intune. You need to configure Intune to meet the following requirements:
✑ Prevent users from enrolling personal devices.
✑ Ensure that users can enroll a maximum of 10 devices.
What should you use for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.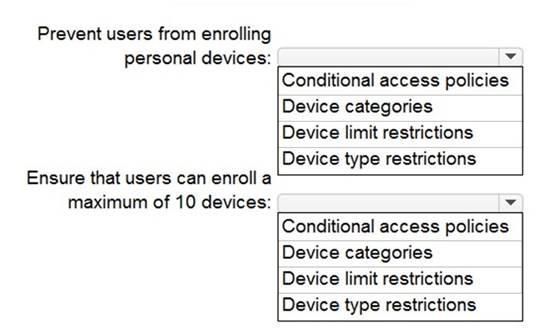
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
You have a Microsoft 365 subscription that uses Security & Compliance retention policies.
You implement a preservation lock on a retention policy that is assigned to all executive users.
Which two actions can you perform on the retention policy? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point?
- A. Add locations to the policy
- B. Reduce the duration of policy
- C. Remove locations from the policy
- D. Extend the duration of the policy
- E. Disable the policy
Answer: AB
NEW QUESTION 9
Your company has 10,000 users who access all applications from an on-premises data center.
You plan to create a Microsoft 365 subscription and to migrate data to the cloud. You plan to implement directory synchronization.
User accounts and group accounts must sync to Azure AD successfully. You discover that several user accounts fail to sync to Azure AD.
You need to resolve the issue as quickly as possible. What should you do?
- A. From Active Directory Administrative Center, search for all the users, and then modify the properties of the user accounts.
- B. Run idfix.exe, and then click Edit.
- C. From Windows PowerShell, run the start-AdSyncSyncCycle -PolicyType Delta command.
- D. Run idfix.exe, and then click Complete.
Answer: B
Explanation:
IdFix is used to perform discovery and remediation of identity objects and their attributes in an on-premises Active Directory environment in preparation for migration to Azure Active Directory. IdFix is intended for the Active Directory administrators responsible for directory synchronization with Azure Active Directory.
Reference:
https://docs.microsoft.com/en-us/office365/enterprise/prepare-directory-attributes-for- synch-with-idfix
NEW QUESTION 10
You need to create the Microsoft Store for Business. Which user can create the store?
- A. User2
- B. User3
- C. User4
- D. User5
Answer: C
Explanation:
References:
https://docs.microsoft.com/en-us/microsoft-store/roles-and-permissions-microsoft-store-for- business
NEW QUESTION 11
You have a Microsoft 365 tenant.
Company policy requires that all Windows 10 devices meet the following minimum requirements:
✑ Require complex passwords.
✑ Require the encryption of data storage devices.
✑ Have Microsoft Defender Antivirus real-time protection enabled.
You need to prevent devices that do not meet the requirements from accessing resources in the tenant.
Which two components should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. a configuration policy
- B. a compliance policy
- C. a security baseline profile
- D. a conditional access policy
- E. a configuration profile
Answer: BD
Explanation:
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
NEW QUESTION 12
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.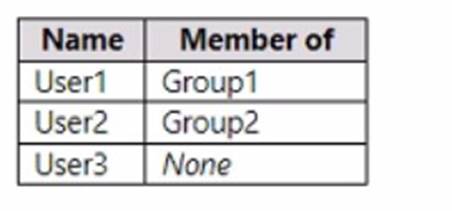
You create an administrative unit named AU1 that contains the members shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.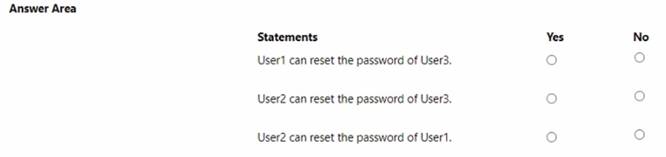
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft intune. The subscription contains the resources shown in the following table.
User1 is the owner of Device1.
You add Microsoft 365 Apps Windows 10 and later app types to Intune as shown in the following table.
On Thursday, you review the results of the app deployments.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Solution:

Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
You have a Microsoft 365 subscription.
You configure a new Azure AD enterprise application named App1. App1 requires that a user be assigned the Reports Reader role.
Which type of group should you use to assign the Reports Reader role and to access App1?
- A. a Microsoft 365 group that has assigned membership
- B. a Microsoft 365 group that has dynamic user membership
- C. a security group that has assigned membership
- D. a security group that has dynamic user membership
Answer: C
Explanation:
To grant permissions to assignees to manage users and group access for a specific enterprise app, go to that app in Azure AD and open in the Roles and Administrators list for
that app. Select the new custom role and complete the user or group assignment. The assignees can manage users and group access only for the specific app.
Note: You can add the following types of groups:
Assigned groups - Manually add users or devices into a static group.
Dynamic groups (Requires Azure AD Premium) - Automatically add users or devices to user groups or device groups based on an expression you create.
Note:
Security groups
Security groups are used for granting access to Microsoft 365 resources, such as SharePoint. They can make administration easier because you need only administer the group rather than adding users to each resource individually.
Security groups can contain users or devices. Creating a security group for devices can be used with mobile device management services, such as Intune.
Security groups can be configured for dynamic membership in Azure Active Directory, allowing group members or devices to be added or removed automatically based on user attributes such as department, location, or title; or device attributes such as operating system version.
Security groups can be added to a team.
Microsoft 365 Groups can't be members of security groups. Microsoft 365 Groups
Microsoft 365 Groups are used for collaboration between users, both inside and outside your company. With each Microsoft 365 Group, members get a group email and shared workspace for conversations, files, and calendar events, Stream, and a Planner.
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/roles/custom-enterprise-apps https://learn.microsoft.com/en-us/microsoft-365/admin/create-groups/compare-groups? https://learn.microsoft.com/en-us/mem/intune/apps/apps-deploy
NEW QUESTION 15
From the Security & Compliance admin center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)
What will be excluded from the export?
- A. a 10-MB XLSX file
- B. a 5-MB MP3 file
- C. a 5-KB RTF file
- D. an 80-MB PPTX file
Answer: B
Explanation:
Unrecognized file formats are excluded from the search.
Certain types of files, such as Bitmap or MP3 files, don't contain content that can be indexed. As a result, the search indexing servers in Exchange and SharePoint don't perform full-text indexing on these types of files. These types of files are considered to be
unsupported file types.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/partially-indexed-items-in-content-search?view=o365-worldwide
https://docs.microsoft.com/en-us/office365/securitycompliance/export-a-content-search- report
NEW QUESTION 16
......
Thanks for reading the newest MS-102 exam dumps! We recommend you to try the PREMIUM Dumps-files.com MS-102 dumps in VCE and PDF here: https://www.dumps-files.com/files/MS-102/ (463 Q&As Dumps)