All About 100% Correct N10-009 Free Draindumps
Want to know Examcollection N10-009 Exam practice test features? Want to lear more about CompTIA CompTIA Network+ Exam certification experience? Study Guaranteed CompTIA N10-009 answers to Improved N10-009 questions at Examcollection. Gat a success with an absolute guarantee to pass CompTIA N10-009 (CompTIA Network+ Exam) test on your first attempt.
Free N10-009 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
Which of the following can be used to decrease latency during periods of high utilization of a firewall?
- A. Hot site
- B. NIC teaming
- C. HA pair
- D. VRRP
Answer: B
Explanation:
NIC Teaming, also known as load balancing and failover (LBFO), allows multiple network adapters on a computer to be placed into a team for the following purposes:
(https://www.bing.com/search?q=what+is+nic+teaming+used+for%3F&form=QBLH&sp=- 1&pq=what+is+nic+teaming+used+for&sc=10- 28&qs=n&sk=&cvid=13882A9A9B584D8099F4ABCAD034E821&ghsh=0&ghacc=0&ghpl=)
NEW QUESTION 2
A firewall administrator is implementing a rule that directs HTTP traffic to an internal server listening on a non-standard socket Which of the following types of rules is the administrator implementing?
- A. NAT
- B. PAT
- C. STP
- D. SNAT
- E. ARP
Answer: B
Explanation:
The firewall administrator is implementing a PAT (Port Address Translation) rule that directs HTTP traffic to an internal server listening on a non-standard socket. PAT is a type of NAT (Network Address Translation) that allows multiple devices to share a single public IP address by using different port numbers. PAT can also be used to redirect traffic from one port to another port on the same or different IP address. This can be useful for security or load balancing purposes. For example, a firewall administrator can configure a PAT rule that redirects HTTP traffic (port 80) from the public IP address of the firewall to an internal server that listens on a non-standard port (such as 8080) on its private IP address. References: https://www.cisco.com/c/en/us/support/docs/ip/network-address- translation-nat/13772-12.html
NEW QUESTION 3
A city has hired a new employee who needs to be able to work when traveling at home and at the municipal sourcing of a neighboring city that snares services. The employee is issued a laptop, and a technician needs to train the employee on the appropriate solutions
for secure access to the network from all the possible locations On which of the following solutions would the technician MOST likely train the employee?
- A. Site-to-site VPNs between the two city locations and client-to-site software on the employee's laptop tor all other remote access
- B. Client-to-site VPNs between the travel locations and site-to-site software on the employee's laptop for all other remote access
- C. Client-to-site VPNs between the two city locations and site-to-site software on the employee's laptop for all other remote access
- D. Site-to-site VPNs between the home and city locations and site-to-site software on the employee's laptop for all other remote access
Answer: A
Explanation:
The technician would most likely train the employee on using site-to-site VPNs between the two city locations and client-to-site software on the employee’s laptop for all other remote access. A VPN (Virtual Private Network) is a technology that creates a secure and encrypted tunnel over a public network such as the Internet. It allows remote users or sites to access a private network as if they were directly connected to it. A site-to- site VPN connects two or more networks, such as branch offices or data centers, using a VPN gateway device at each site. A client-to-site VPN connects individual users, such as mobile workers or telecommuters, using a VPN client software on their devices. In this scenario, the employee needs to access the network from different locations, such as home, travel, or another city. Therefore, the technician would train the employee on how to use site-to-site VPNs to connect to the network from another city location that shares services, and how to use client-to-site software to connect to the network from home or travel locations. References: https://www.cisco.com/c/en/us/support/docs/security- vpn/ipsec-negotiation-ike-protocols/14106-how-vpn-works.html
NEW QUESTION 4
A virtual machine has the following configuration:
· IPv4 address: 169.254.10.10
· Subnet mask: 255.255.0.0
The virtual machine can reach colocated systems but cannot reach external addresses on the internet. Which of the following is most likely the root cause?
- A. The subnet mask is incorrect.
- B. The DHCP server is offline.
- C. The IP address is an RFC1918 private address.
- D. The DNS server is unreachable.
Answer: B
Explanation:
The IP address 169.254.10.10 is an APIPA (Automatic Private IP Addressing) address, which is assigned by the operating system when a DHCP server is not available or reachable. APIPA addresses are in the range of 169.254.0.0/16, and they allow the device to communicate with other devices on the same local network, but not with external networks or the internet. Therefore, the most likely root cause of the virtual machine’s connectivity issue is that the DHCP server is offline or malfunctioning, and the virtual machine cannot obtain a valid IP address from it.
References
✑ 1: CompTIA Network+ N10-008 Certification Study Guide, page 86
✑ 2: CompTIA Network+ N10-008 Exam Subnetting Quiz, question 9
✑ 3: CompTIA Network+ N10-008 Certification Practice Test, question 4
NEW QUESTION 5
A network technician is selecting a replacement for a damaged fiber cable that goes directly to an SFP transceiver on a network switch. Which of the following cable connectors should be used?
- A. RJ45
- B. LC
- C. MT
- D. F-type
Answer: C
NEW QUESTION 6
A technician notices that equipment is being moved around and misplaced in the server room, even though the room has locked doors and cabinets. Which of the following would be the BEST solution to identify who is responsible?
- A. Install motion detection
- B. Install cameras.
- C. Install tamper detection.
- D. Hire a security guard.
Answer: B
Explanation:
Installing cameras in the server room is the best solution to identify who is responsible for the equipment being moved and misplaced. Cameras provide a way to monitor the server room in real time and can be used to identify suspicious activity. Additionally, they provide a way to review past activity and allow you to review footage to determine who may be responsible for the misplacement of equipment.
NEW QUESTION 7
A network administrator is required to ensure that auditors have read-only access to the system logs, while systems administrators have read and write access to the system logs, and operators have no access to the system logs. The network administrator has configured security groups for each of these functional categories. Which of the following security capabilities will allow the network administrator to maintain these permissions with the LEAST administrative effort?
- A. Mandatory access control
- B. User-based permissions
- C. Role-based access
- D. Least privilege
Answer: C
Explanation:
Role-based access is a security capability that assigns permissions to users based on their roles or functions within an organization. It allows the network administrator to maintain these permissions with the least administrative effort, as they only need to configure the security groups for each role once and then assign users to those groups. Mandatory access control is a security capability that assigns permissions based on security labels or classifications, which requires more administrative effort to maintain. User-based permissions are a security capability that assigns permissions to individual users, which is not scalable or efficient for large organizations. Least privilege is a security principle that states that users should only have the minimum level of access required to perform their tasks, which is not a security capability by itself.
NEW QUESTION 8
A network administrator responds to a support ticket that was submitted by a customer who is having issues connecting to a website inside of the company network The administrator verities that the customer could not connect to a website using a URL Which of the following troubleshooting steps would be BEST for the administrator to take?
- A. Check for certificate issues
- B. Contact the ISP
- C. Attempt to connect to the site via IP address
- D. Check the NTP configuration.
Answer: C
Explanation:
The best option for the administrator to take would be to attempt to connect to the site via IP address. This will help to determine if the issue is related to the website's DNS address or if the site itself is not accessible. Checking for certificate issues may be necessary, but this should be done after the administrator has attempted to connect to the site via IP address. Contacting the ISP is unnecessary since the issue is related to the website inside of the company network, and checking the NTP configuration is not relevant to this issue.
When a customer is having issues connecting to a website using a URL, one of the first troubleshooting steps a network administrator should take is attempting to connect to the site using the IP address of the website. This will help to determine if the issue is related to a DNS resolution problem or a connectivity problem. If the administrator is able to connect to the website using the IP address, then the issue may be related to a DNS problem. However, if the administrator is still unable to connect, then the issue may be related to a connectivity problem. In either case, further troubleshooting steps will be necessary. Checking for certificate issues or NTP configuration, and contacting the ISP would not be the BEST initial steps in this scenario.
NEW QUESTION 9
A network technician was troubleshooting an issue for a user who was being directed to cloned websites that were stealing credentials. The URLs were correct for the websites but an incorrect IP address was revealed when the technician used ping on the user's PC After checking the is setting, the technician found the DNS server address was incorrect Which of the following describes the issue?
- A. Rogue DHCP server
- B. Misconfigured HSRP
- C. DNS poisoning
- D. Exhausted IP scope
Answer: C
Explanation:
DNS poisoning is a type of attack that modifies the DNS records of a domain name to point to a malicious IP address instead of the legitimate one. This can result in users being directed to cloned websites that are stealing credentials, even if they enter the correct URL for the website. The incorrect DNS server address on the user’s PC could be a sign of DNS poisoning, as the attacker could have compromised the DNS server or spoofed its response to redirect the user’s queries. References: https://www.comptia.org/blog/what-is-dns-poisoning
NEW QUESTION 10
Which of the following, in addition to a password, can be asked of a user for MFA?
- A. PIN
- B. Favorite color
- C. Hard token
- D. Mother's maiden name
Answer: A
Explanation:
MFA stands for Multi-Factor Authentication, which is a method of verifying the identity of a user by requiring two or more pieces of evidence that belong to different categories: something the user knows, something the user has, or something the user is. A password is something the user knows, and it is usually combined with another factor such as a PIN (Personal Identification Number) or a hard token (a physical device that generates a one- time code) that the user has. A favorite color or a mother’s maiden name are not suitable for MFA, as they are also something the user knows and can be easily guessed or compromised.
References
✑ 1: Multi-Factor Authentication – N10-008 CompTIA Network+ : 3.1
✑ 2: CompTIA Network+ Certification Exam Objectives, page 13
✑ 3: CompTIA Network+ N10-008 Certification Study Guide, page 250
✑ 4: CompTIA Network+ N10-008 Exam Subnetting Quiz, question 14
NEW QUESTION 11
An ISP configured an internet connection to provide 20Mbps, but actual data rates are occurring at 10Mbps and causing a significant delay in data transmission. Which of the following specifications should the ISP check?
- A. Throughput
- B. Latency
- C. Bandwidth
- D. Jitter
Answer: A
Explanation:
Throughput is the actual amount of data that can be transferred over a network in a given time. Throughput can be affected by various factors such as congestion, interference, errors, or hardware limitations. If the throughput is lower than the configured internet connection speed, it can cause a significant delay in data transmission. The ISP should check the throughput and identify the source of the problem.
References: Network+ Study Guide Objective 2.2: Explain the concepts and characteristics of routing and switching.
NEW QUESTION 12
A company has multiple offices around the world. The computer rooms in some office locations are too warm Dedicated sensors are in each room, but the process of checking each sensor takes a long time. Which of the following options can the company put In place to automate temperature readings with internal resources?
- A. Implement NetFlow.
- B. Hire a programmer to write a script to perform the checks
- C. Utilize ping to measure the response.
- D. Use SNMP with an existing collector server
Answer: D
Explanation:
SNMP (Simple Network Management Protocol) is a protocol that allows network devices to communicate with a management server. By using SNMP, the company can set up an SNMP agent on each sensor, which will report its temperature readings to an existing collector server. This will enable the company to monitor the temperatures of all their sensors in real-time without the need for manual checks. Additionally, SNMP's scalability means that even if the company adds more rooms or sensors, the existing system can be easily expanded to accommodate them.
NEW QUESTION 13
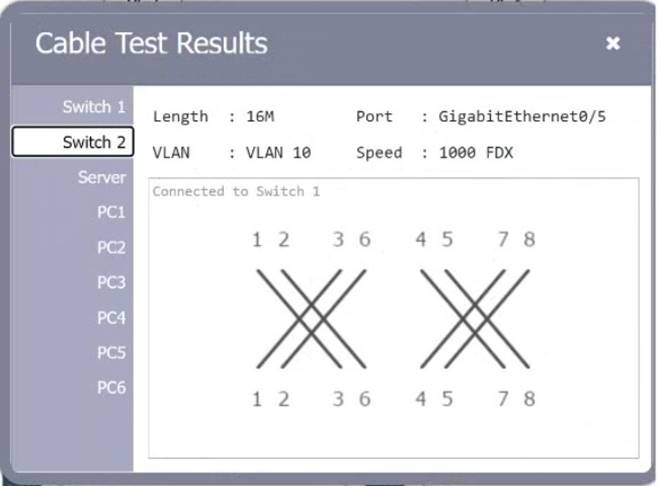
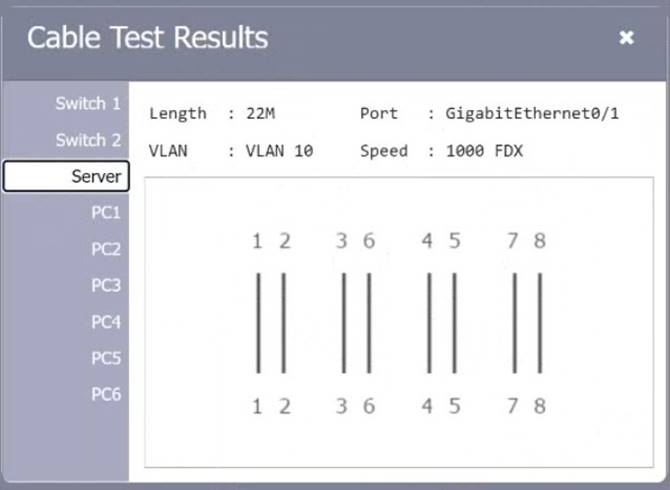
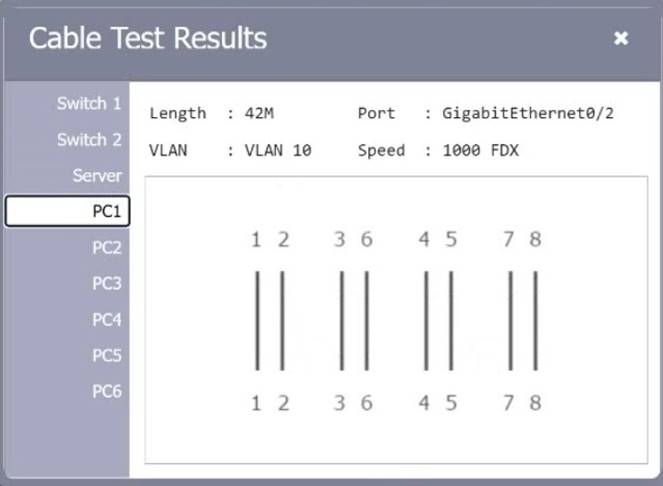
SIMULATION
A network technician needs to resolve some issues with a customer's SOHO network. The customer reports that some of the PCs are not connecting to the network, while others appear to be working as intended.
INSTRUCTIONS
Troubleshoot all the network components.
Review the cable test results first, then diagnose by clicking on the appropriate PC, server, and Layer 2 switch.
Identify any components with a problem and recommend a solution to correct each problem.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.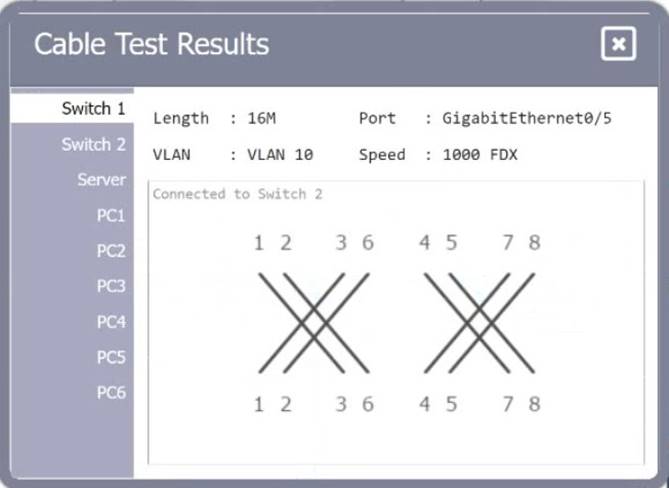
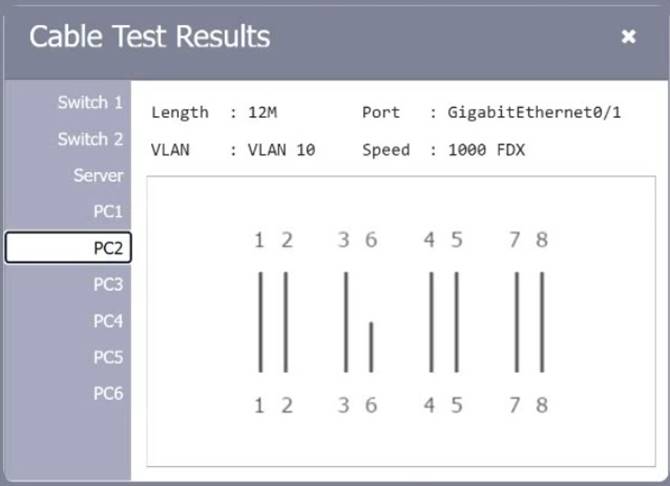
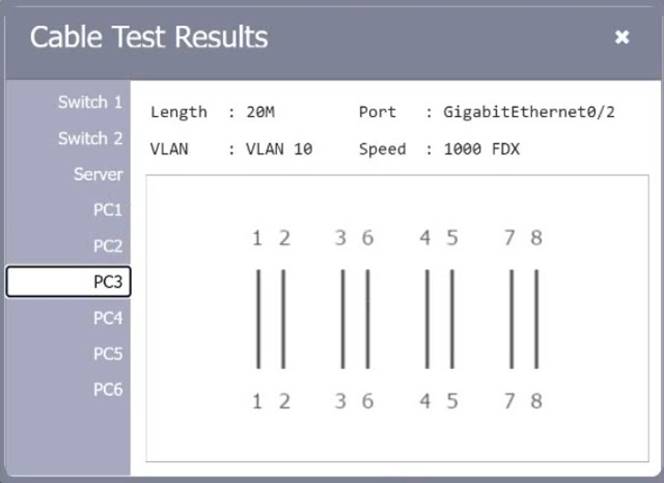
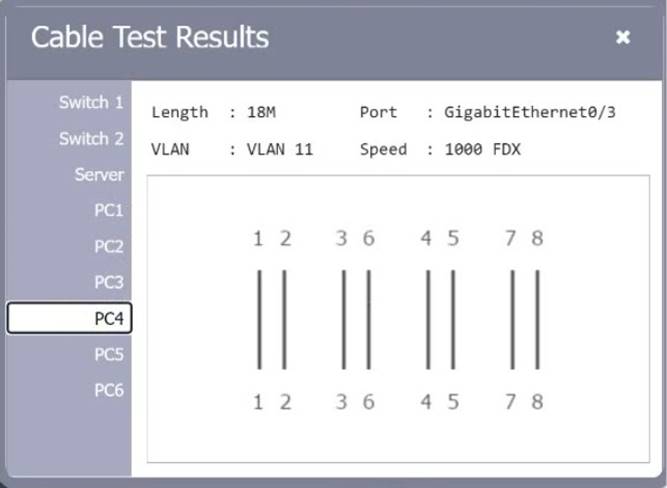
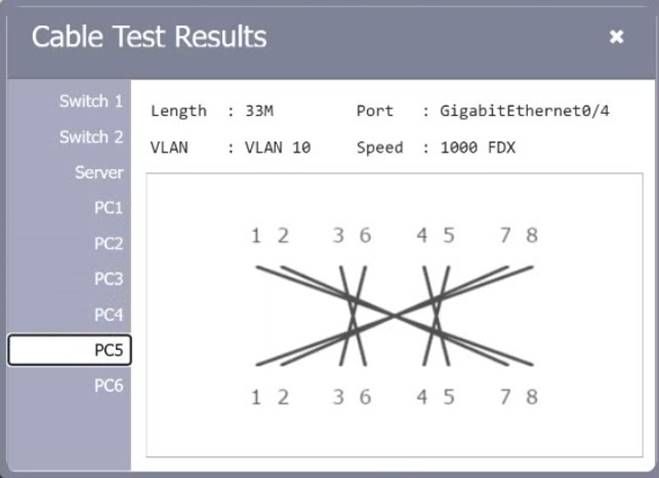
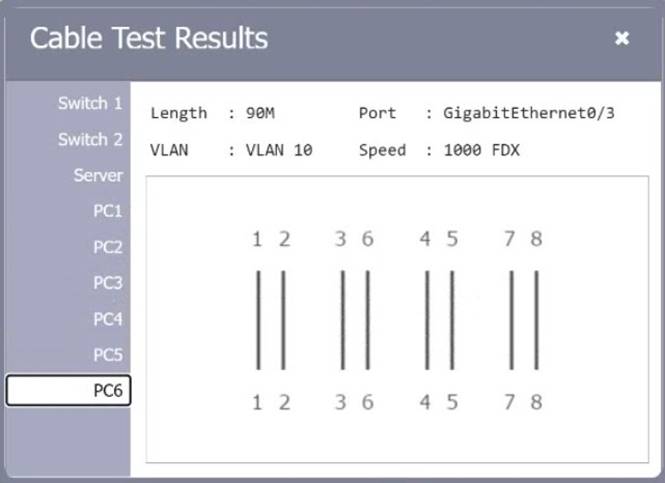
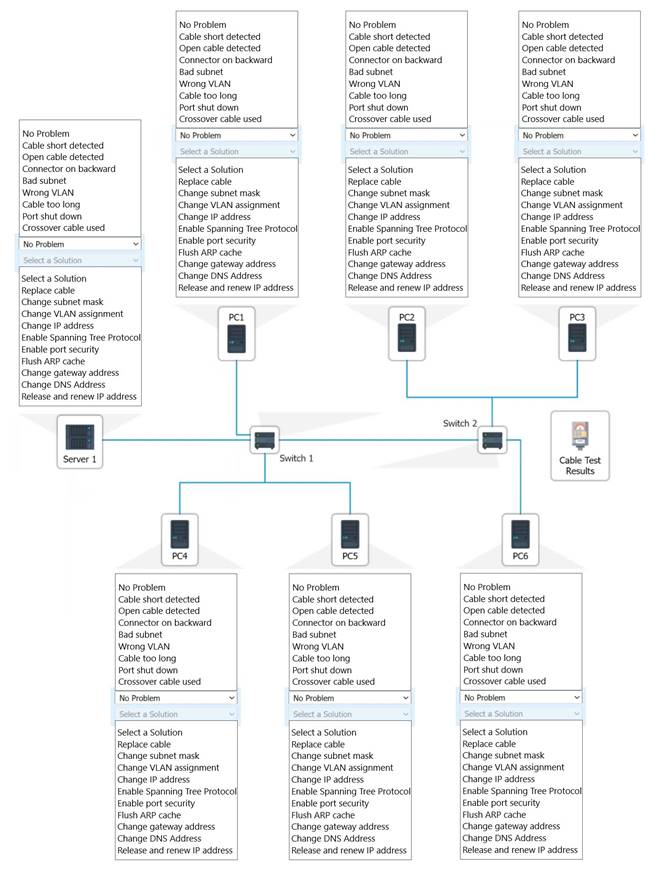
Solution:
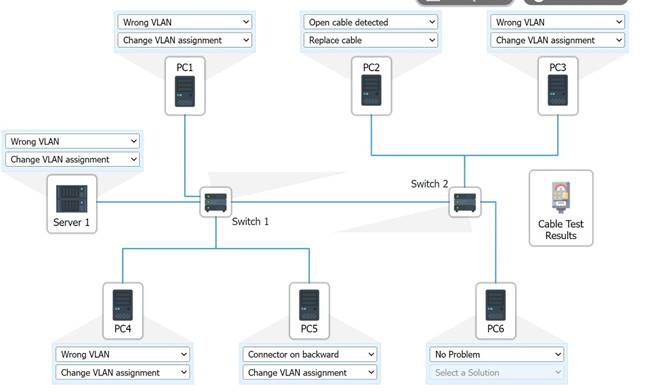
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
Which of the following layers of the OSI model receives data from the application layer and converts it into syntax that is readable by other devices on the network?
- A. Layer 1
- B. Layer 3
- C. Layer 6
- D. Layer 7
Answer: C
NEW QUESTION 15
Which of the following is most likely to be implemented to actively mitigate intrusions on a host device?
- A. HIDS
- B. MDS
- C. HIPS
- D. NIPS
Answer: A
Explanation:
HIDS (host-based intrusion detection system) is a type of security software that monitors and analyzes the activity on a host device, such as a computer or a server. HIDS can detect and alert on intrusions, such as malware infections, unauthorized access, configuration changes, or policy violations. HIDS can also actively mitigate intrusions by blocking or quarantining malicious processes, files, or network connections1.
HIPS (host-based intrusion prevention system) is similar to HIDS, but it can also prevent intrusions from happening in the first place by enforcing security policies and rules on the host device2. MDS (multilayer switch) is a network device that combines the functions of a switch and a router, and it does not directly protect a host device from intrusions3. NIPS (network-based intrusion prevention system) is a network device that monitors and blocks malicious traffic on the network level, and it does not operate on the host device level4.
NEW QUESTION 16
Within the realm of network security, Zero Trust:
- A. prevents attackers from moving laterally through a system.
- B. allows a server to communicate with outside networks without a firewall.
- C. block malicious software that is too new to be found in virus definitions.
- D. stops infected files from being downloaded via websites.
Answer: A
Explanation:
Zero Trust is a security framework that requires all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust prevents attackers from moving laterally through a system by applying granular policies and controls based on the principle of least privilege and by segmenting and encrypting data flows across the network. References: https://partners.comptia.org/docs/default-source/resources/comptia-network-n10-008- exam-objectives-(2-0), https://www.crowdstrike.com/cybersecurity-101/zero-trust-security/
NEW QUESTION 17
Users ate moving back into an office that had been vacant for awhile. Ten workstations are hooked up in the office, but one workstation cannot obtain a link with (he switch. A network engineer checks the documentation and cable labeling, and everything is hooked up as expected. The engineer moves the connection lo a different switchport. but a link still cannot be obtained. When the engineer puts a tone generator on (he infrastructure cable, no tone is heard at the far end. Which of the following issues is the engineer MOST likely trying to find?
- A. A bad switchport
- B. A break in the cable
- C. A cable short
- D. Cable interference
Answer: B
Explanation:
A break in the cable means that there is no electrical continuity between the two ends of the cable, which prevents the signal from reaching the switch. A tone generator is a device that sends an audible signal through the cable, and if no tone is heard at the far end, it indicates a break in the cable.
NEW QUESTION 18
A global company has acquired a local company. The companies are geographically separate. The IP address ranges for the two companies are as follows:
· Global company: 10.0.0.0/16
· Local company: 10.0.0.0/24
Which of the following can the network engineer do to quickly connect the two companies?
- A. Assign static routing to advertise the local company's network.
- B. Assign an overlapping IP address range to both companies.
- C. Assign a new IP address range to the local company.
- D. Assign a NAT range to the local company.
Answer: C
Explanation:
Assigning a new IP address range to the local company is the best option to quickly connect the two companies without causing any IP address conflicts or overlaps. This option requires reconfiguring the local company’s network devices and updating the routing tables on both sides, but it avoids the need for any NAT or static routing solutions that may introduce additional complexity, cost, or performance issues12 References1: Connecting Networks with Overlapping IP Ranges 2: What Is Network Address Translation (NAT)?
NEW QUESTION 19
A network administrator is implementing process changes based on recommendations following a recent penetration test. The testers used a method to gain access to the network that involved exploiting a publicly available and fixed remote code execution vulnerability in the VPN appliance. Which of the following should the administrator do to BEST prevent this from happening again?
- A. Change default passwords on internet-facing hardware.
- B. Implement robust ACLs with explicit deny-all entries.
- C. Create private VLANs for management plane traffic.
- D. Routinely upgrade all network equipment firmware.
Answer: D
Explanation:
Firmware is the software that runs on network equipment such as routers, switches, and VPN appliances. Firmware updates often contain bug fixes, security patches, and performance improvements that can prevent or mitigate vulnerabilities and attacks. By routinely upgrading all network equipment firmware, a network administrator can ensure that the network devices are running the latest and most secure versions of firmware and avoid exploiting known and fixed remote code execution vulnerabilities in the VPN appliance. References: https://www.comptia.org/training/books/network-n10-008-study- guide (page 462)
NEW QUESTION 20
A network administrator installed a new data and VoIP network. Users are now experiencing poor call quality when making calls. Which of the following should the administrator do to increase VoIP performance?
- A. Configure a voice VLAN.
- B. Configure LACP on all VoIP phones.
- C. Configure PoE on the network.
- D. Configure jumbo frames on the network.
Answer: A
Explanation:
"Benefits of Voice VLAN
It ensures that your VoIP (Voice over Internet Phone) devices do not have to contend directly with all the broadcasts and other traffic from the data VLAN. A voice VLAN can simplify network configuration in some circumstances."
https://community.fs.com/blog/auto-voip-vs-voice-vlan-what-s-the-difference.html Jumbo Frames
"When jumbo frames on a VoIP/UC network are enabled, it can cause the same kind of
delay to your network transmissions."
"VoIP uses will always not benefit from jumbo frame, as VoIP like gaming, is latency and time sensitive. Jumbo Frame for Internet Purpose: You will not see any performance boost as the files that came across the internet does not support jumbo frame."
https://www.ankmax.com/newsinfo/1358641.html#:~:text=VoIP%20uses%20will%20always
%20not,does%20not%20support%20jumbo%20frame.
"To summarize this general best practice guide, you should NOT enable jumbo frame feature as a general home user."
NEW QUESTION 21
......
100% Valid and Newest Version N10-009 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/N10-009-exam-dumps.html (New 179 Q&As)